The latest updated leads4pass 312-50v11 dumps with PDF files and VCE exam engine, containing 528 exam questions and answers, serve all 312-50v11 CEH v11 exam candidates to help them successfully pass the exam.
You are welcome to download the latest updated 312-50v11 dumps: https://www.leads4pass.com/312-50v11.html, you will also enjoy 365 days of free updates and a 15% discount with discount code “EC-COUNCIL”.
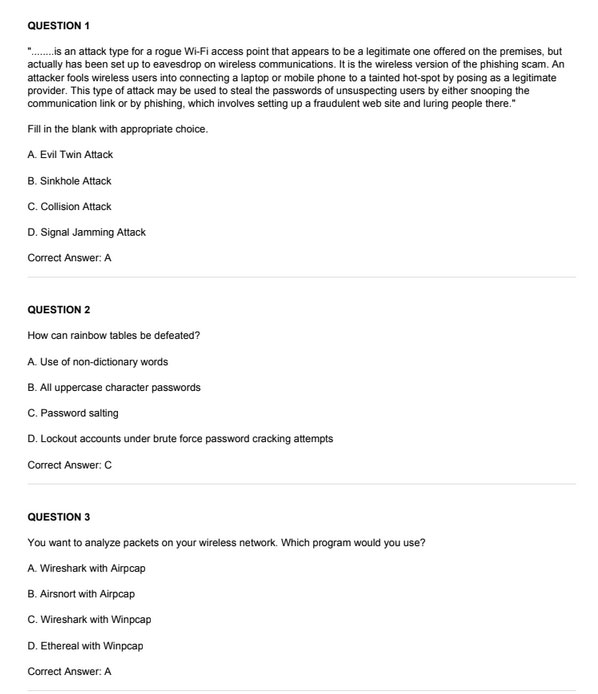
Check out the leads4pass 312-50v11 dumps PDF example image:

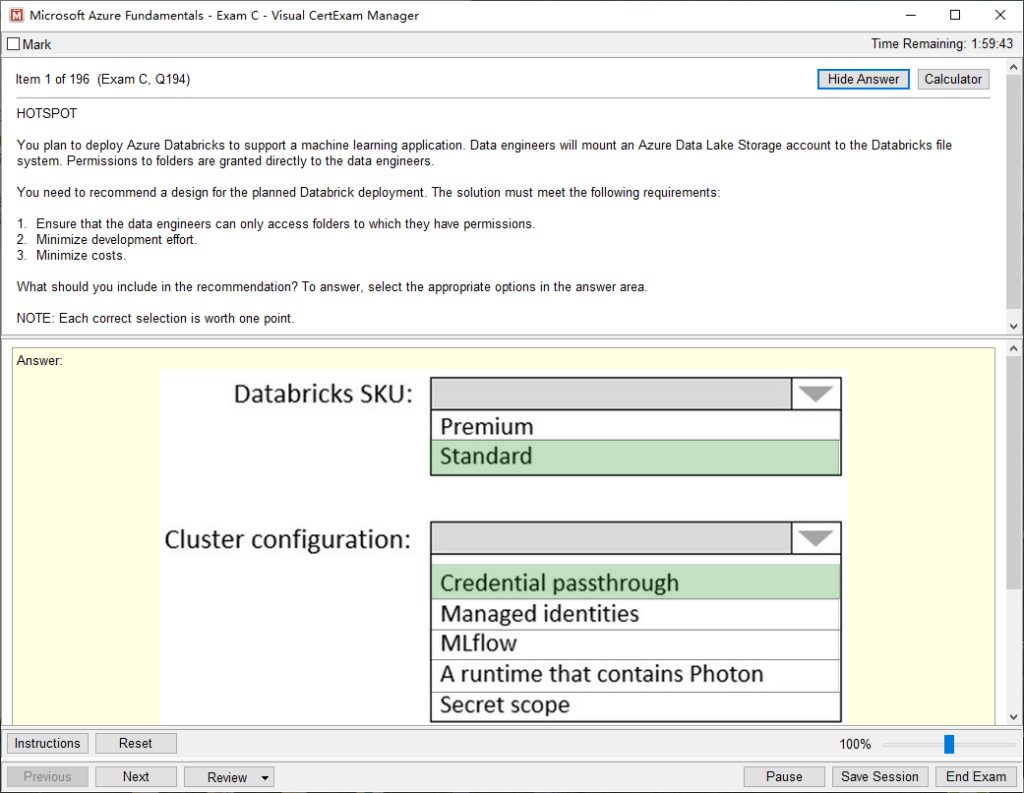
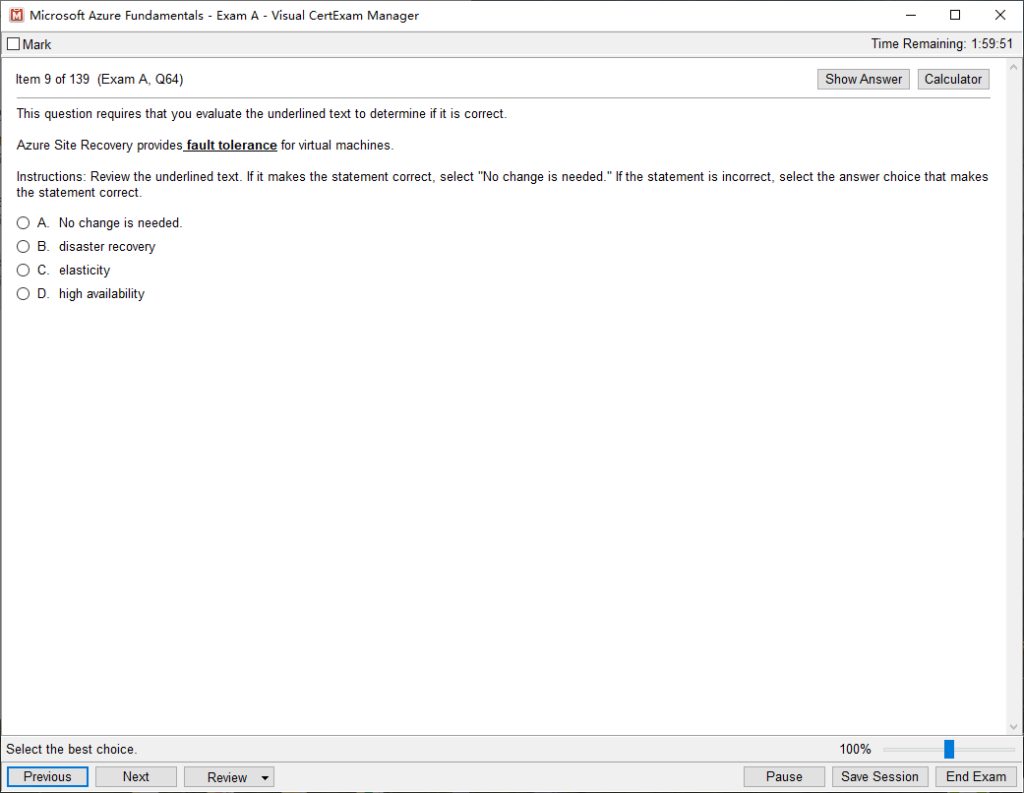
Check out the leads4pass 312-50v11 dumps VCE example image:
Download all free 2022 EC-COUNCIL 312-50v11 dumps PDF online:
https://drive.google.com/file/d/1IW-vsqqsN4-yp3ZoNmhIm42BJE6y58_m/
Free sharing of 15 EC-COUNCIL 312-50v11 Dumps exam questions and answers:
New Question 1:
When configuring wireless on his home router, Javik disables SSID broadcast. He leaves authentication “open” but sets the SSID to a 32-character string of random letters and numbers.
» Read more about: Leads4Pass 312-50v11 dumps with PDF and VCE latest update »
Continue reading...