The most valuable experience provided by multiple successful CyberOps Professional 350-201 certification exam candidates, sharing how to successfully pass this exam.
This article uses ChatGPT to answer all the questions that CyberOps Professional 350-201 Certification candidates care about. It is really smart and helps us save more time and provide the most accurate and effective answers. And the latest useful ones provided by Lead4Pass certification exam questions and answers,Really help the follow-up people to pass the exam successfully.

Is the CyberOps Professional 350-201 exam difficult?
The difficulty level of the CyberOps Professional 350-201 exam can vary from person to person and depends on factors such as their prior experience and knowledge in the field, preparation time, and study habits. However, in general, the 350-201 exam is considered to be a challenging certification exam that tests a candidate’s ability to understand and apply complex cybersecurity concepts.
It is recommended to have hands-on experience and a thorough understanding of the exam content and format before taking the exam.

Best Ways to Take the CyberOps Professional 350-201 Certification Exam
To prepare for the CyberOps Professional 350-201 certification exam, here are some best practices:
1. Study the exam objectives and familiarize yourself with the exam format and content.
2. Use Cisco’s official course materials and study resources, such as the “Implementing and Operating Cisco Security Core Technologies (SCOR)” course and the Cisco CyberOps Associate certification exam guide.
3. Practical experience with the relevant technology is essential. Consider setting up a lab environment or using a simulation tool for practice. Welcome to Lead4Pass 350-201 Dumps: https://www.leads4pass.com/350-201.html which includes PDF study files and VCE practice exam tools to help you study for success with ease.
4. Join study groups or online forums to collaborate with others and discuss questions and best practices.
5. Regularly take practice exams to gauge your understanding of the material and identify areas where you need more study.
6. Stay current with industry developments and updates by regularly reading relevant blogs, whitepapers, and other resources.
Remember, the more you practice, the better prepared you’ll be for the exam. Good luck!

What are the CyberOps Professional 350-201 exam details?
1. The Cisco CyberOps Professional 350-201 certification exam is a 120-minute, 65-75 multiple choice, and simulation-based test.
2. The exam is designed to measure the candidate’s ability to understand, analyze and respond to security threats in a complex network environment.
3. The topics covered in the exam include security concepts, security monitoring, security incidents, analysis, and response procedures.
4. The minimum passing score for the exam is not publicly disclosed by Cisco.
5. The exam is available in English and Japanese languages and can be taken at any Cisco-authorized testing center or online through the Pearson VUE platform.
CyberOps Professional 350-201 Online Practice
| Type | Number of exam questions | Exam name | Exam code | Exam answers |
| Free | 15 | Performing CyberOps Using Cisco Security Technologies (CBRCOR) | 350-201 | View |
Question 1:
A company\’s web server availability was breached by a DDoS attack and was offline for 3 hours because it was not deemed a critical asset in the incident response playbook. Leadership has requested a risk assessment of the asset. An analyst conducted the risk assessment using the threat sources, events, and vulnerabilities.
Which additional element is needed to calculate the risk?
A. assessment scope
B. event severity and likelihood
C. incident response playbook
D. risk model framework
Question 2:
DRAG DROP
Drag and drop the threat from the left onto the scenario that introduces the threat on the right. Not all options are used.
Select and Place:
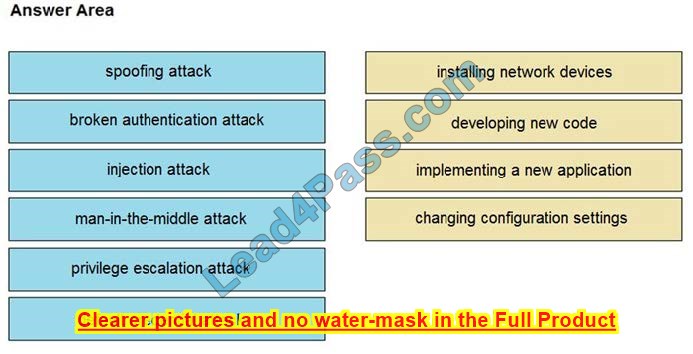
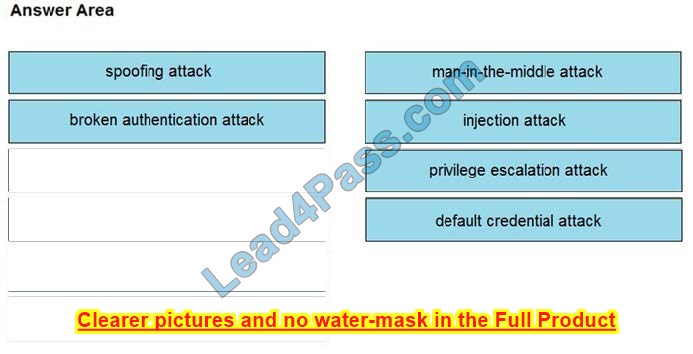
Correct Answer:
Question 3:
A Mac laptop user notices that several files have disappeared from their laptop documents folder. While looking for the files, the user notices that the browser history was recently cleared. The user raises a case, and an analyst reviews the network usage and discovers that it is abnormally high.
Which step should be taken to continue the investigation?
A. Run the sudo sys diagnose command
B. Run the sh command
C. Run the w command
D. Run the who command
Reference: https://eclecticlight.co/2016/02/06/the-ultimate-diagnostic-tool-sysdiagnose/
Question 4:
An engineer receives an incident ticket with hundreds of intrusion alerts that require investigation. An analysis of the incident log shows that the alerts are from trusted IP addresses and internal devices. The final incident report stated that these alerts were false positives and that no intrusions were detected.
What action should be taken to harden the network?
A. Move the IPS to after the firewall facing the internal network
B. Move the IPS to before the firewall facing the outside network
C. Configure the proxy service on the IPS
D. Configure reverse port forwarding on the IPS
Question 5:
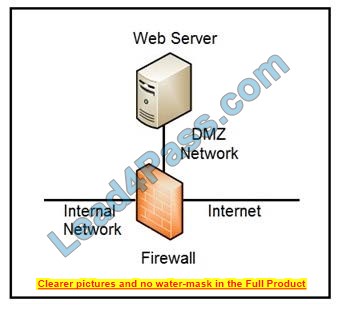
Refer to the exhibit. Which two steps mitigate attacks on the webserver from the Internet? (Choose two.)
A. Create an ACL on the firewall to allow only TLS 1.3
B. Implement a proxy server in the DMZ network
C. Create an ACL on the firewall to allow only external connections
D. Move the webserver to the internal network
Question 6:
An organization had an incident with the network availability during which devices unexpectedly malfunctioned. An engineer is investigating the incident and found that the memory pool buffer usage reached a peak before the malfunction. Which action should the engineer take to prevent this issue from reoccurring?
A. Disable memory limit.
B. Disable CPU threshold trap toward the SNMP server.
C. Enable memory tracking notifications.
D. Enable memory threshold notifications.
Question 7:
Refer to the exhibit. An engineer is performing static analysis of a file received and reported by a user. Which risk is indicated in this STIX?
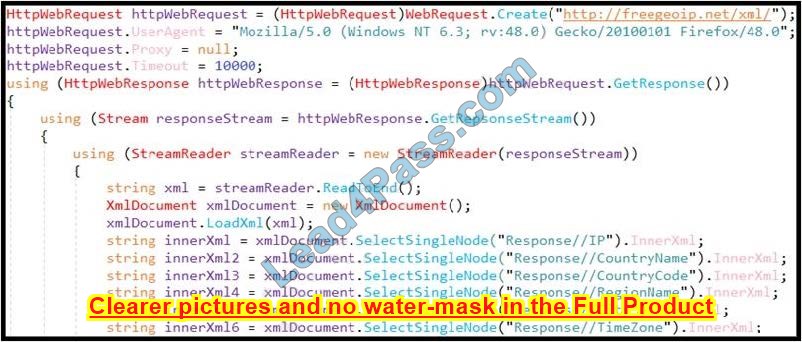
A. The file is redirecting users to a website that requests privilege escalations from the user.
B. The file is redirecting users to the website that is downloading ransomware to encrypt files.
C. The file is redirecting users to a website that harvests cookies and stored account information.
D. The file redirects users to a website that is determining users’ geographic location.
Question 8:
An analyst is alerted for a malicious file hash. After analysis, the analyst determined that an internal workstation is communicating over port 80 with an external server and that the file hash is associated with Duqu malware. Which tactics, techniques, and procedures align with this analysis?
A. Command and Control, Application Layer Protocol, Duqu
B. Discovery, Remote Services: SMB/Windows Admin Shares, Duqu
C. Lateral Movement, Remote Services: SMB/Windows Admin Shares, Duqu
D. Discovery, System Network Configuration Discovery, Duqu
Question 9:
An analyst received multiple alerts on the SIEM console of users that are navigating to malicious URLs. The analyst needs to automate the task of receiving alerts and processing the data for further investigations. Three variables are available from the SIEM console to include in an automation script: console_ip, api_token, and reference_set_name. What must be added to this script to receive a successful HTTP response?
#!/usr/bin/pythonimport sysimport requests
A. {1}, {2}
B. {1}, {3}
C. console_ip, api_token
D. console_ip, reference_set_name
Question 10:
A company recently completed an internal audit and discovered that there is CSRF vulnerability in 20 of its hosted applications. Based on the audit, which recommendation should an engineer make for patching?
A. Identify the business applications running on the assets
B. Update software to patch third-party software
C. Validate CSRF by executing exploits within Metasploit
D. Fix applications according to the risk scores
Question 11:
DRAG DROP
Drag and drop the function on the left onto the mechanism on the right.
Select and Place:
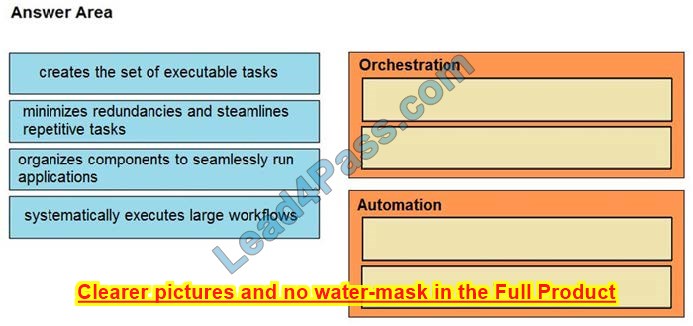
Correct Answer:
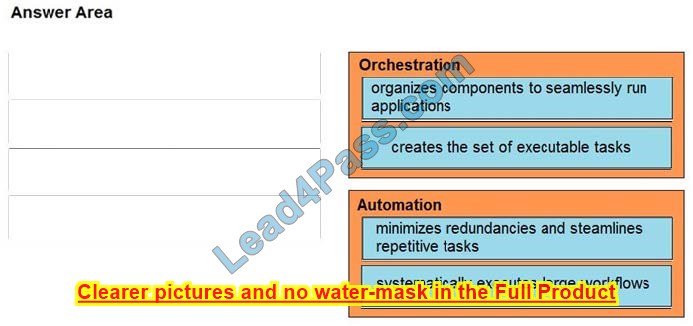
Question 12:
A security architect is working in a processing center and must implement a DLP solution to detect and prevent any type of copy-and-paste attempts of sensitive data within unapproved applications and removable devices. Which technical architecture must be used?
A. DLP for data in motion
B. DLP for removable data
C. DLP for data in use
D. DLP for data at rest
Reference: https://www.endpointprotector.com/blog/what-is-data-loss-prevention-dlp/
Question 13:
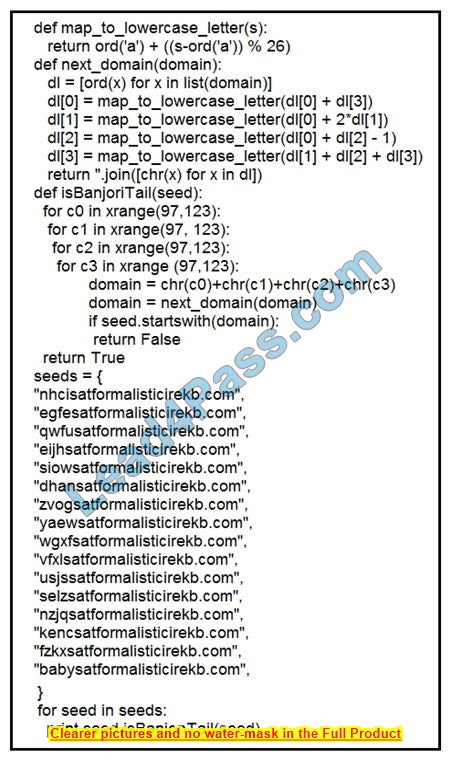
Refer to the exhibit. What results from this script?
A. Seeds for existing domains are checked
B. A search is conducted for additional seeds
C. Domains are compared to seed rules
D. A list of domains as seeds is blocked
Question 14:
What is needed to assess risk mitigation effectiveness in an organization?
A. analysis of key performance indicators
B. compliance with security standards
C. cost-effectiveness of control measures
D. an updated list of vulnerable systems
Question 15:
Patient views information that is not theirs when they sign in to the hospital\’s online portal. The patient calls the support center at the hospital but continues to be put on hold because other patients are experiencing the same issue. An incident has been declared, and an engineer is now on the incident bridge as the CyberOps Tier 3 Analyst. There is a concern about the disclosure of PII occurring in real time.
What is the first step the analyst should take to address this incident?
A. Evaluate visibility tools to determine if external access resulted in tampering
B. Contact the third-party handling provider to respond to the incident as critical
C. Turn off all access to the patient portal to secure patient records
D. Review system and application logs to identify errors in the postal code
…
View 139 latest valid CyberOps Professional 350-201 exam questions and answers, and download Lead4Pass 350-201 dumps 2023: https://www.leads4pass.com/350-201.html, to help you pass the exam successfully.
CyberOps Professional 350-201 exam answers
| Q1 | Q2 | Q3 | Q4 | Q5 | Q6 | Q7 | Q8 | Q9 | Q10 | Q11 | Q12 | Q13 | Q14 | Q15 |
| D | IMAGE | A | C | BD | D | D | A | C | D | IMAGE | C | B | C | C |
Is the CyberOps Professional 350-201 certification exam worth it?
The value of a certification exam such as the CyberOps Professional 350-201 depends on individual goals and career aspirations.
In general, certifications can demonstrate a level of knowledge and skills in a specific area, which can be attractive to potential employers. They can also provide opportunities for professional growth and can increase earning potential.
However, the value of a certification is subjective and varies based on individual circumstances and the current job market demand for the skills and knowledge tested in the exam. It’s important to weigh the cost and time investment of obtaining certification against its potential benefits.

Rewards for successfully passing the CyberOps Professional 350-201 certification exam
Upon successful completion of the Cisco 350-201 CyberOps Professional certification exam, the following rewards are typically achieved:
1. Recognition of expertise in cybersecurity operations and threat detection.
2. Improved job prospects and higher earning potential in the cybersecurity field.
3. Validation of skills and knowledge in cybersecurity operations and analysis.
4. Access to a network of professionals in the cybersecurity industry.
5. Increased credibility and confidence in performing cybersecurity operations.
6. Opportunities for advancement and leadership in the cybersecurity field.
7. Possibility of increased responsibilities and opportunities for professional growth.
