How do I get CompTIA Security+ 2022 SY0-601 exam success?
Was able to successfully pass the CompTIA Security+ 2022 SY0-601 exam on the first attempt, as lead4Pass’s newly updated SY0-601 dumps April 2022 latest version is now available. Amazon Certified CompTIA Security+ 2022 SY0-601 Dumps Lead4Pass exam questions and answers can effectively improve your skills and help you succeed.
SY0-601 Dumps not only help you provide adequate preparation, but are also a valid goal for you to prepare for the actual SY0-601 CompTIA Security+ 2022 exam. Select SY0-601 dumps: https://www.leads4pass.com/sy0-601.html for the actual purpose.
[Practice Test] CompTIA Security+ 2022 SY0-601 Free Dumps Read First
The questions for SY0-601 were last updated on April 25, 2022.
Viewing questions 1-13 out of 572 questions:
QUESTION 1:
A company was recently breached Part of the company\’s new cybersecurity strategy is to centralize the logs from all security devices Which of the following components forwards the logs to a central source?
A. Log enrichment
B. Log aggregation
C. Log parser
D. Log collector
Correct Answer: D
QUESTION 2:
An end-user reports a computer has been acting slower than normal for a few weeks, During an investigation, an analyst determines the system 3 sending the users email address and a ten-digit number ta an IP address once a day.
The only recent log entry regarding the user\’s computer is the following:

Which of the following is the MOST likely cause of the issue?
A. The end-user purchased and installed 2 PUP from a web browser.
B. 4 bot on the computer is ruled forcing passwords against a website.
C. A hacker Is attempting to exfiltrate sensitive data.
D. Ransomware is communicating with a command-and-control server.
Correct Answer: A
QUESTION 3:
An enterprise needs to keep cryptographic keys in a safe manner. Which of the following network appliances can achieve this goal?
A. HSM
B. CASB
C. TPM
D. DLP
Correct Answer: A
A hardware security module (HSM) is a security device you can add to a system to manage, generate, and securely store cryptographic keys. High-performance HSMs are external devices connected to a network using TCP/IP. Smaller HSMs come as expansion cards you install within a server, or as devices, you plug into computer ports.
QUESTION 4:
An attack relies on an end-user visiting a website the end-user would typically visit, however, the site is compromised and uses vulnerabilities in the end user’s browser to deploy malicious software. Which of the blowing types of attack does this describe?
A. Smishing
B. Whaling
C. Watering hole
D. Phishing
Correct Answer: C
QUESTION 5:
A financial analyst is expecting an email containing sensitive information from a client. When the email arrives, the analyst receives an error and is unable to open the encrypted message. Which of the following is the MOST likely cause of the issue?
A. The S/MME plug-in is not enabled.
B. The SSL certificate has expired.
C. Secure IMAP was not implemented
D. POP3S is not supported.
Correct Answer: A
QUESTION 6:
To reduce costs and overhead, an organization wants to move from an on-premises email solution to a cloud-based email solution. At this time, no other services will be moving. Which of the following cloud models would BEST meet the needs of the organization?
A. Maas
B. laaS
C. SaaS
D. PaaS
Correct Answer: D
QUESTION 7:
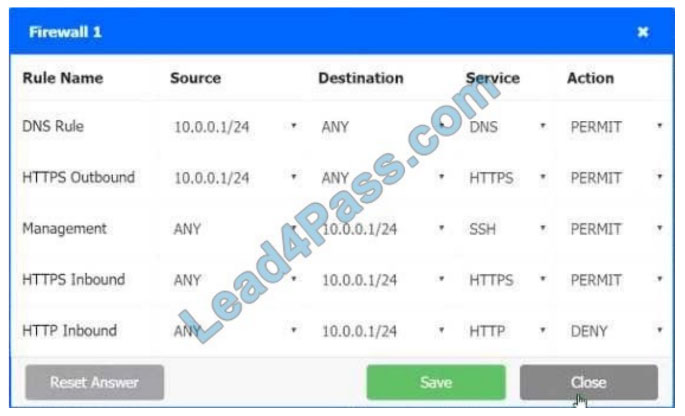
SIMULATION
A company recently added a DR site and is redesigning the network. Users at the DR site are having issues browsing websites.
INSTRUCTIONS
Click on each firewall to do the following:
1.
Deny cleartext web traffic.
2.
Ensure secure management protocols are used.
3.
Resolve issues at the DR site.
The ruleset order cannot be modified due to outside constraints.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
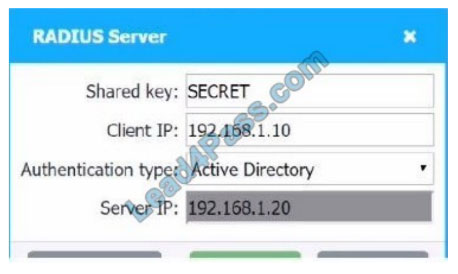
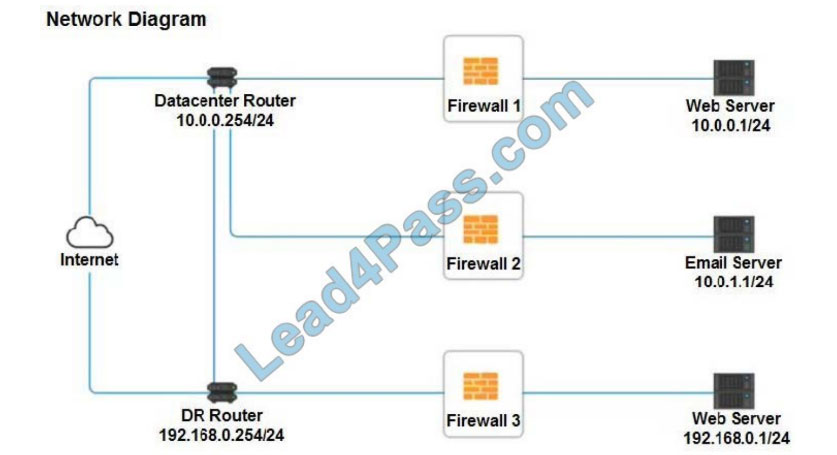
Firewall 1
Hot Area:
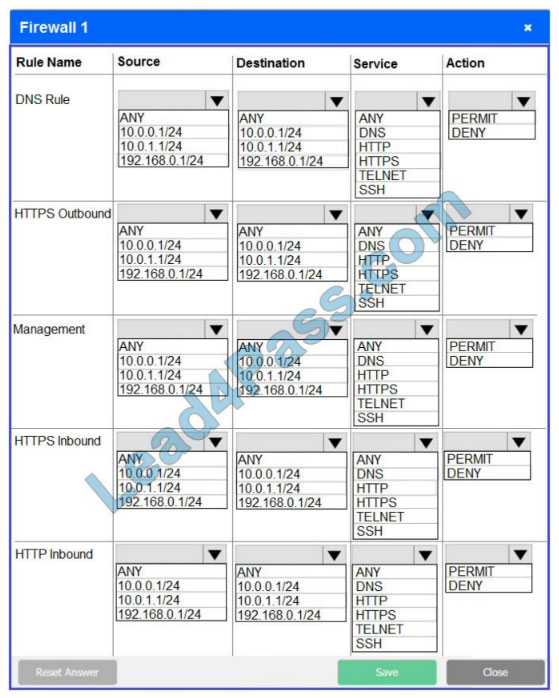
Correct Answer:
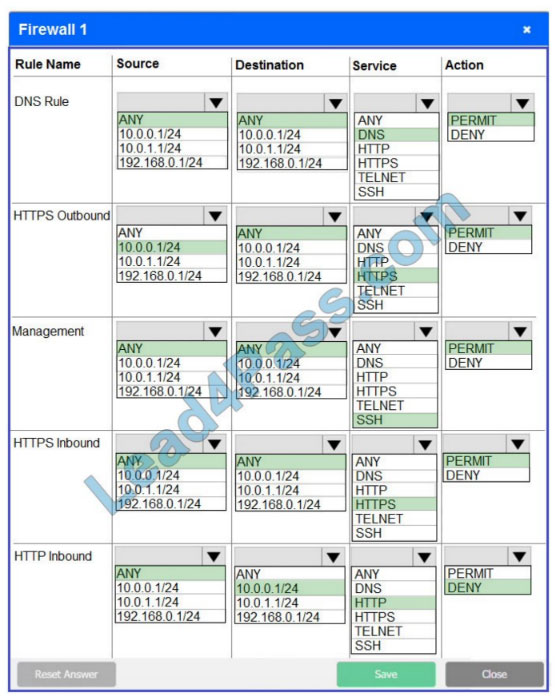
In Firewall 1, HTTP inbound Action should be DENY. As shown below
QUESTION 8:
A company Is concerned about its security after a red-team exercise. The report shows the team was able to reach the critical servers due to the SMB being exposed to the Internet and running NTLMV1. Which of the following BEST explains the findings?
A. Default settings on the servers
B. Unsecured administrator accounts
C. Open ports and services
D. Weak Data encryption
Correct Answer: C
QUESTION 9:
Several employees have noticed other bystanders can clearly observe a terminal where passcodes are being entered.
Which of the following can be eliminated with the use of a privacy screen?
A. Shoulder surfing
B. Spear phishing
C. Impersonation attack
D. Card cloning
Correct Answer: A
QUESTION 10:
Customers reported their antivirus software flagged one of the company\’s primary software products as suspicious. The company\’s Chief Information Security Officer has tasked the developer with determining a method to create a trust model between the software and the customer\’s antivirus software. Which of the following would be the BEST solution?
A. Code signing
B. Domain validation
C. Extended validation
D. Self-signing
Correct Answer: C
QUESTION 11:
Which of the following corporate policies is used to help prevent employee fraud and to detect system log modifications or other malicious activity based on tenure?
A. Background checks
B. Mandatory vacation
C. Social media analysis
D. Separation of duties
Correct Answer: B
QUESTION 12:
A company\’s Chief Information Security Officer (CISO) recently warned the security manager that the company\’s Chief Executive Officer (CEO) is planning to publish a controversial option article in a national newspaper, which may result in new cyberattacks Which of the following would be BEST for the security manager to use in a threat model?
A. Hacktivists
B. White-hat hackers
C. Script kiddies
D. Insider threats
Correct Answer: A
Hacktivists – “a person who gains unauthorized access to computer files or networks in order to further social or political ends.”
QUESTION 13:
A company has three technicians who share the same credentials for troubleshooting the system. Every time credentials are changed, the new ones are sent by email to all three technicians. The security administrator has become aware of this situation and wants to implement a solution to mitigate the risk. Which of the following is the BEST solution for a company to implement?
A. SSO authentication
B. SSH keys
C. OAuth authentication
D. Password vaults
Correct Answer: A
Reference: https://www.onelogin.com/learn/how-single-sign-on-works
……
[Google Drive] CompTIA Security+ 2022 SY0-601 Free Dumps Online Download:https://drive.google.com/file/d/1_Q4ZV-dIBnxY5N3xpETOiNf4cRTQRC1P/view?usp=sharing
Why Choose Lead4Pass SY0-601 Dumps?
Lead4Pass SY0-601 Dumps develops authentic and valid exam questions along with answers and explanations to help you progress based on the core objectives of the CompTIA Security+ 2022 exam. And provide PDF and VCE two learning tools, any choice to help you complete the CompTIA Security+ 2022 SY0-601 exam objectives. Use the SY0-601 dumps of the latest version in April 2022: https://www.leads4pass.com/sy0-601.html. 572 exam questions and answers to easily pass the exam.
