You can take your CompTIA Cybersecurity Analyst exam by studying the latest CS0-002 dumps.
Choose to get CS0-002 dumps to complete your CompTIA CySA+ certification exam.
It is recommended to choose Lead4Pass CS0-002 dumps https://www.leads4pass.com/cs0-002.html online for reading. All the exam questions and answers in CS0-002 exam dumps are required to be read and memorized well to make sure you can pass the CompTIA CySA+ exam successfully.
Download the latest CompTIA CySA+ CS0-002 dumps PDF: https://drive.google.com/file/d/19qVA35_5E-QX1yT4zU_JANR3wsQAYNu0/
Read the latest CompTIA CySA+ CS0-002 dumps exam questions and answers online
| Number of exam questions | Exam name | From | Release time | Last updated |
| 15 | CompTIA Cybersecurity Analyst (CySA+) | Lead4Pass | Dec 06, 2022 | CS0-002 dumps |
NEW QUESTION 1:
Due to new regulations, a company has decided to institute an organizational vulnerability management program and assign the function to the security team. Which of the following frameworks would BEST support the program? (Choose two.)
A. COBIT
B. NIST
C. ISO 27000 series
D. ITIL
E. COSO
Correct Answer: BD
NEW QUESTION 2:
A malicious hacker wants to gather guest credentials on a hotel 802.11 network. Which of the following tools is the malicious hacker going to use to gain access to information found on the hotel network?
A. Nikto
B. Aircrak-ng
C. Nessus
D. tcpdump
Correct Answer: B
NEW QUESTION 3:
A company\’s Chief Information Security Officer (CISO) published an Internet usage policy that prohibits employees from accessing unauthorized websites. The IT department whitelisted websites used for business needs.
The CISO wants the security analyst to recommend a solution that would improve security and support employee morale. Which of the following security recommendations would allow employees to browse non-business-related websites?
A. Implement a virtual machine alternative.
B. Develop a new secured browser.
C. Configure a personal business VLAN.
D. Install kiosks throughout the building.
Correct Answer: C
NEW QUESTION 4:
A security analyst reviews SIEM logs and detects a well-known malicious executable running on a Windows machine.
The up-to-date antivirus cannot detect the malicious executable. Which of the following is the MOST likely cause of this issue?
A. The malware is lifeless and exists only in physical memory
B. The malware detects and prevents its own execution in a virtual environment
C. The antivirus does not have the malware\’s signature
D. The malware is being executed with administrative privileges
Correct Answer: D
NEW QUESTION 5:
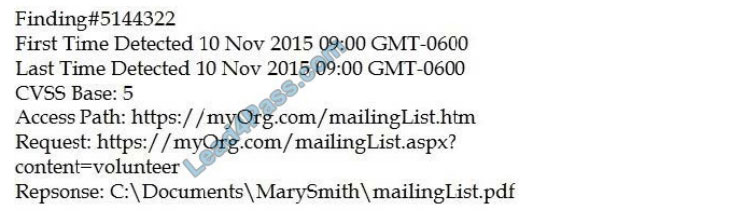
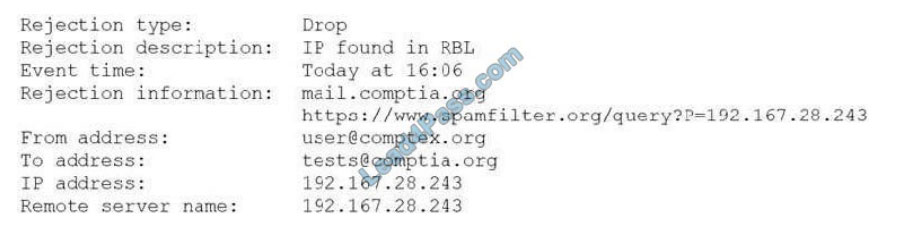
An organization is attempting to harden its web servers and reduce the information that might be disclosed by potential attackers. A security analyst is reviewing vulnerability scan results from a recent web server scan.
Portions of the scan results are shown below:
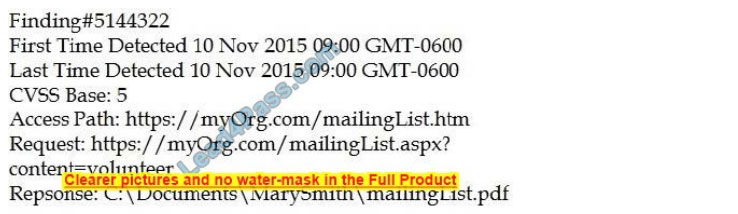
Which of the following lines indicates information disclosure about the host that needs to be remediated?
A. Response: :\Documents\MarySmith\mailingList.pdf
B. Finding#5144322
C. First Time Detected 10 Nov 2015 09:00 GMT-0600
D. Access Path: http://myOrg.com/mailingList.htm
E. Request: GET http://myOrg.com/mailingList.aspx?content=volunteer
Correct Answer: A
NEW QUESTION 6:
To validate local system-hardening requirements, which of the following types of vulnerability scans would work BEST to verify the scanned device meets security policies?
A. SCAP
B. SAST
C. DAST
D. DACS
Correct Answer: A
NEW QUESTION 7:
A security administrator determines several months after the first instance that a local privileged user has been routinely logging into a server interactively as “root” and browsing the Internet.
The administrator determines this by performing an annual review of the security logs on that server. For which of the following security architecture areas should the administrator recommend review and modification? (Select TWO).
A. Log aggregation and analysis
B. Software assurance
C. Encryption
D. Acceptable use policies
E. Password complexity
F. Network isolation and separation
Correct Answer: AD
NEW QUESTION 8:
While conducting research on malicious domains, a threat intelligence analyst received a blue screen of death. The analyst rebooted and received a message stating that the computer had been locked and could only be opened by following the instructions on the screen.
Which of the following combinations describes the MOST likely threat and the PRIMARY mitigation for the threat?
A. Ransomware and update antivirus
B. Account takeover and data backups
C. Ransomware and full disk encryption
D. Ransomware and data backups
Correct Answer: D
NEWW QUESTION 9:
A security analyst discovers the accounting department is hosting an accounts receivable form on a public document service. Anyone with the link can access it. Which of the following threats applies to this situation?
A. Potential data loss to external users
B. Loss of public/private key management
C. Cloud-based authentication attack
D. Insufficient access logging
Correct Answer: A
NEW QUESTION 10:
Which of the following are the MOST likely reasons to include reporting processes when updating an incident response plan after a breach? (Select TWO).
A. To establish a clear chain of command
B. To meet regulatory requirements for timely reporting
C. To limit reputation damage caused by the breach
D. To remediate vulnerabilities that led to the breach
E. To isolate potential insider threats
F. To provide secure network design changes
Correct Answer: BF
NEW QUESTION 11:
As part of the senior leadership team\’s ongoing risk management activities the Chief Information Security Officer has tasked a security analyst with coordinating the right training and testing methodology to respond to new business initiatives or significant changes to existing ones The management team wants to examine a new business process that would use existing infrastructure to process and store sensitive data.
Which of the following would be appropriate for the security analyst to coordinate?
A. A black-box penetration testing engagement
B. A tabletop exercise
C. Threat modeling
D. A business impact analysis
Correct Answer: D
NEW QUESTION 12:
Which of the following commands would a security analyst use to make a copy of an image for forensics use?
A. dd
B. wget
C. touch
D. rm
Correct Answer: A
NEW QUESTION 13:
While analyzing network traffic, a security analyst discovers several computers on the network are connecting to a malicious domain that was blocked by a DNS sinkhole. A new private IP range is now visible, but no change requests were made to add it.
Which of the following is the BEST solution for the security analyst to implement?
A. Block the domain IP at the firewall.
B. Blacklist the new subnet
C. Create an IPS rule.
D. Apply network access control.
Correct Answer: A
…
Get 919 newly updated CS0-002 dumps exam questions and answers to complete the CompTIA Cybersecurity Analyst certification exam with Lead4Pass CS0-002 dumps https://www.leads4pass.com/cs0-002.html.
BTW, Download free latest CompTIA CySA+ CS0-002 dumps PDF above: https://drive.google.com/file/d/19qVA35_5E-QX1yT4zU_JANR3wsQAYNu0/